What Is Rocky Linux? Rocky Linux is an open source Linux distribution that supports the Red Hat Enterprise Linux (RHEL) operating system source code. It offers a downstream, binary-compatible release for production-grade RHEL with community support. It was developed by the Rocky Enterprise Software Foundation and was made generally available on […]
This Article Only For Education Purpose Don’t try Real World WhatsApp is the most widely used social app being used by people around the world to communicate, or as the younger generation likes to call it, ‘chat’ with their colleagues, family, and friends. It is a convenient way to communicate […]
MD5 Message Digest Algorithm, or MD5, is a cryptographic hashing function. It is a part of the Message Digest Algorithm family which was created to verify the integrity of any message or file that is hashed. MD5 is still used in a few cases; however, MD5 is insecure and should not […]
Introduction¶ Owasp Php configuring and the web server it is running on to be very secure. Below you will find information on the proper settings for the php.ini file and instructions on configuring Apache, Nginx, and Caddy web servers. For general PHP codebase security please refer to the two following great guides: […]
What is a Denial of Service Attacks? A Denial of Service Attacks (DoS) attack occurs when legitimate users are unable to access information systems, devices, or other network resources due to the actions of a malicious cyber threat actor. Services affected may include email, websites, online accounts (e.g., banking), or […]
Juice Jacking Attack one of the most recent and most creative ways of penetrating PC frameworks.It includes a generally neglected escape clause allowing an aggressor to directadmittance to your frameworks. In this piece, we’ll investigate thesignificance, history, types, and working rules of juice jacking. Juice jacking is a framework weakness […]
Man-in-the-middle attacks (MITM) can be executed in a number of different ways that exploit communications between other parties. Whether by passive or active means, an MITM attack finds a way between a user and an entity and attempts to conceal the breach and information theft. Below are common ways Man-in-the-Middle […]
In this article, I am going to list a few such deprecated Linux commands. ou may still find a few of them in your distribution. Believe it or not, you might be using a Linux command. Or at least try to use it. It’s not really your fault. You are […]
Reverse IP Lookup: Sharing a host with several web properties isn’t uncommon. In fact, several WordPress and other third-party content platform users are no stranger to the concept. And the practice can put an organisation’s digital assets at risk of malware infection, a breach, a distributed denial-of-service (DDoS) attack, a […]
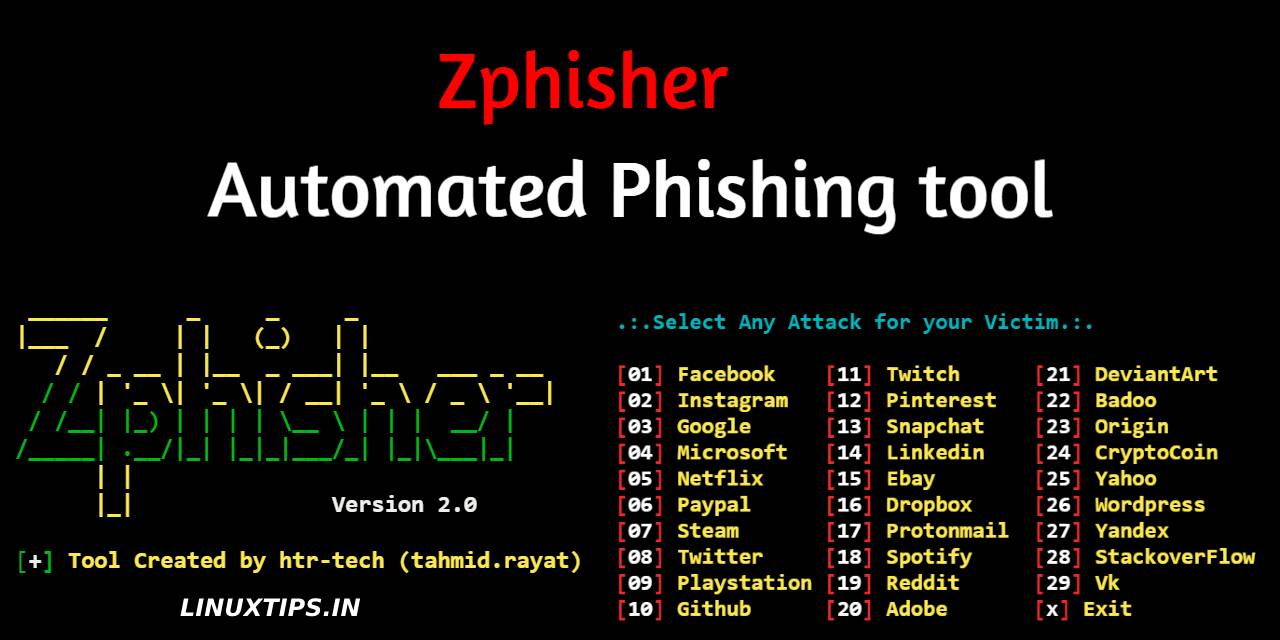
With the increased usage of social media around the globe, stealing of social media credentials by hackers has become a major problem around the globe. The stolen social media credentials are later used to lure and steal money and other valuable from unsuspecting social media users, friends and family. In […]