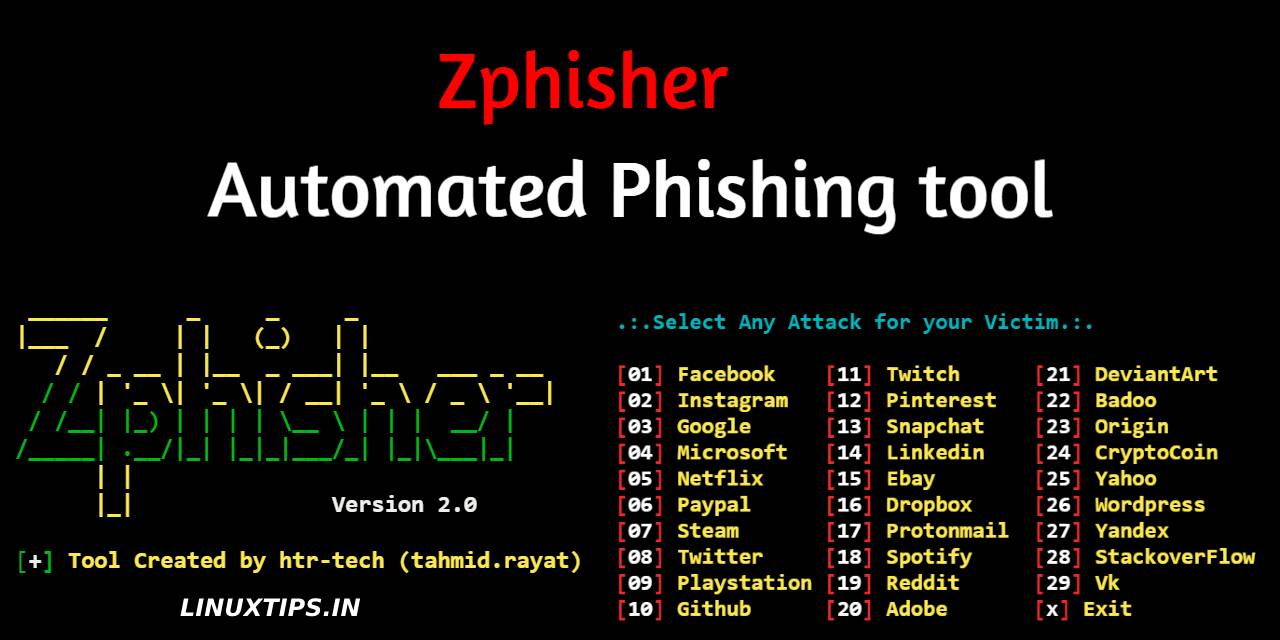
With the increased usage of social media around the globe, stealing of social media credentials by hackers has become a major problem around the globe. The stolen social media credentials are later used to lure and steal money and other valuable from unsuspecting social media users, friends and family. In […]

















